Why the Google Docs Phish Caught Fire

At about 9 a.m. PT, we received an email from a customer that uses G Suite (the artist formerly known as Google Apps for Business) that at first glance looked legitimate.
As you may have read, this took the Internet by storm. If you clicked through the links provided, you granted the phishing app falsely named "Google Docs" permission to your Gmail account. Granting this permission let the phishing app email all your contacts with your Gmail account, helping it spread. The big question is, why was this so successful? 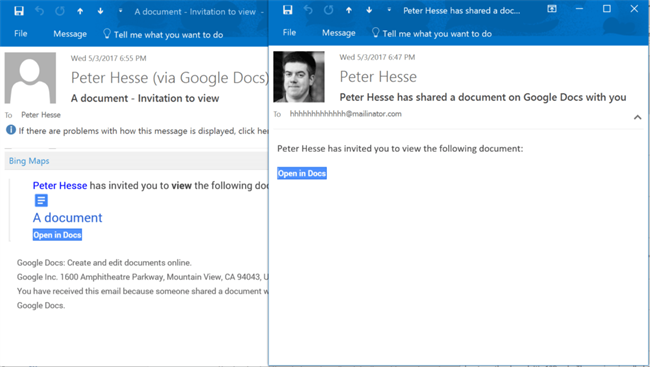
(The real and the phish, side by side.)
This looked to be the most effective email worm since the "ILOVEYOU" virus, which I was tackling back in the year 2000. So, what made it spread so quickly? I believe there are three reasons, which all follow one theme.
1. Reliance on the HTTPS Safety Icons
For better or for worse, I think most people now know that a green check mark in the address bar (HTTPS) means you are at a legitimate site, and a red X or yellow exclamation point (HTTP) causes at least some warning or hesitation. Since this spread through Google's completely legitimate mechanism for granting access to apps, the site was real, the certificate was real, and the browser said so. The creators of this phishing scam were effective in designing something that would look trustworthy and therefore safe.
2. Known Contacts and Known Names
Unlike many phishing schemes, this email did not come from a random person. It came from someone who had you in their contact list. It included not just their real gmail address, but their real first and last name - or whatever is used whenever they email you regularly. You might be surprised, but so many phishing emails can be dismissed out of hand based on the fact you don't know the sender, or there is no name in the email.
3. Cloud Service Ubiquity
Quick - name a service you use that isn't based in the cloud. Can you? Probably not. From your email to your social media, from your messaging to your financial apps, and everything in between - are partially if not entirely hosted in the cloud. Chromebooks exist because people don't need anything more than a Web browser. We don't send attachments anymore, because attachments can carry viruses. Email services block them. So instead, we send links to the documents in our cloud-based services. From OneDrive to SharePoint to Dropbox to Box to Google Docs, we are sharing things in the cloud on a regular basis.
Did you catch on to the theme yet?
- We have taught people to look for the green check mark, and they did.
- We have taught people to only click on links in emails from people that they know, and they did.
- We have taught people to not click attachments but instead use cloud services, and they did.
This phishing attack spread like wildfire because if you follow the advice that security professionals provide, you would click on the link. This was a very clever attack, and it may not be the last. In the meantime, continue to be suspicious. The fact it was sent to a hhhhhhhhhhhh@mailinator.com address was a good giveaway, and people should have also questioned why "Google Docs" would need access to their Gmail account and address book.
(What happened if you clicked through and clicked where it said "Google Docs".)
All in all, I believe this phishing attack helps demonstrate the difference between training and awareness. Someone can be trained to look for a green check mark, or to not click on an attachment - but someone with awareness can be naturally curious enough to suspect this email might not be on the up-and-up.
Perpetrators of these types of attacks are getting much smarter, and it is incumbent upon all of us have more than just training, policies, and procedures. We should go further with ongoing education for all employees to recognize and act upon suspicious activity. A broad spectrum of software, solutions, and education are necessary to counteract the increasing complexity of these threats.
About the Author
Peter Hesse is the chief security officer (CSO) at 10Pearls. Prior to 10Pearls, Hesse founded and ran the successful information security consulting firm Gemini Security Solutions for over a dozen years. He now focuses on avoiding the common break/fix mentality around security, and instead finding ways to architect and build security into systems and products.